
Russia’s invasion of the Ukraine will create new and dangerous cybersecurity threats across the world, industry experts have told Verdict. Russian forces have seized control of Ukrainian airspace and ground troops are moving rapidly to occupy the country, but in the cyber realm the conflict threatens to spread well beyond the national borders.
Cybersecurity experts and government agencies are warning companies, banks and other organisations to prepare for invisible digital assaults.
“Whilst you can see tanks rolling across borders, an invisible war is also being waged,” Dan Davies, CTO at cloud and managed service company Maintel, tells Verdict. “Cyber criminals are now armed to the teeth, with some receiving the backing of rogue states. Consequently, organisations are increasingly outwitted, outgunned and outflanked by hackers.”
The alarm has already been sounded on both sides of the Atlantic. The US Cybersecurity & Infrastructure Security Agency (CISA) has warned all organisations that hacks are coming and that it’s time to put “shields up.” In the UK, the National Cyber Security Centre (NCSC) has similarly cautioned British organisations about the heightened risk of attacks, imploring them to strengthen their digital defences ASAP.
Vladimir Putin’s regime has form when it comes to cyber attacks. Research from cybersecurity company Trellix suggests Russian and Chinese nation-state backed groups were responsible for 46% of all observed advanced persistent threats in the second half of 2021. Nobody would expect the Kremlin to ignore the digital battlefront as it moves to crush Ukraine.
The cyberwar has begun
The cyberwar has already begun. On Wednesday, cybersecurity firm ESET announced the discovery of a new data wiper malware used in Ukraine, named HermeticWiper. ESET said the malware was installed on hundreds of machines in the country. Russia has denied any involvement.
Similar attacks have plagued Ukraine since Russia first invaded the Crimean peninsula in 2014. The most well-known of these attacks happened in December 2015 when Russian state-backed hacking group Sandworm crippled the nation’s power grid, causing outages for roughly 230,000 citizens for up to six hours.
In 2017, Sandworm was allegedly also behind the NotPetya malware attack that paralysed ports, corporations and government agencies around the world.
Both the CISA and the NCSC warned on Wednesday that Sandworm is now back wreaking havoc in Ukraine using a new malware, referred to as Cyclops Blink.
There have also been reports of massive internet disruptions in Ukraine. The Ukraine government has reportedly responded by attempting to enlist its own underground hacking community in the war effort, having had a cybersecurity firm post ads for people to sign up.
US President Joe Biden is reportedly weighing different options to respond to the digital assaults against Ukraine. While no decision has so far been made, US intelligence officials told NBC News that “military cyber warriors are proposing the use of American cyberweapons on a scale never before contemplated.”
The US has already responded with new sanctions designed to choke Russia’s tech sector. The latest sanctions, announced on Thursday, would restrict US tech companies from exporting their products to Russia. The ban would include computers, sensors, lasers, navigation tools and semiconductors. The ban also extends to companies using American products in their own production. Two dozen members of the EU as well as the UK, Canada, Japan, Australia and New Zealand are imposing similar bans, Reuters reported.
These sanctions are also one of the reasons why companies in the West should worry about their firewalls.
“Sanctions on Russia will likely lead to retaliatory attacks,” Adam Seamons, systems and security engineer at IT governance solutions provider GRC International Group, tells Verdict. “Business leaders of critical infrastructure such as the power suppliers, oil, gas, telecoms, and financial services should expect Denial of Service and ransomware style attacks. I’d also expect public services, hospitals and schools to be targeted.”
Will the Ukraine conflict affect Western cybersecurity?
Cyber attacks have so far seemingly been confined mostly to Ukraine. The Polish government’s services fell victim to cyber attacks earlier this week, but the origin of these attacks are still unclear. However, cybersecurity experts warn that it’s only a matter of time before the cyberwar spreads outside of Ukraine. Once unleashed, digital viruses spread just as easily as biological contagions.
“Businesses should be under no illusions: the cybersecurity shock waves from the Ukraine crisis will extend across the world,” Oliver Pinson-Roxburgh, CEO at Defense.com, tells Verdict.
He adds that the company’s financial services and insurances in the UK have seen a “significant step-up in cyber attacks from Russian IP addresses in recent months.”
“The bad actors have been scanning for weaknesses and made several attempts to exploit Oracle systems used by many financial organisations,” Pinson-Roxburgh continues.
The markets seem to agree. Publicly traded cybersecurity companies like Telos, Palo Alto Networks and CrowdStrike saw their shares spike this week while the rest of the stock market slumped and cryptocurrencies‘ value plummeted.
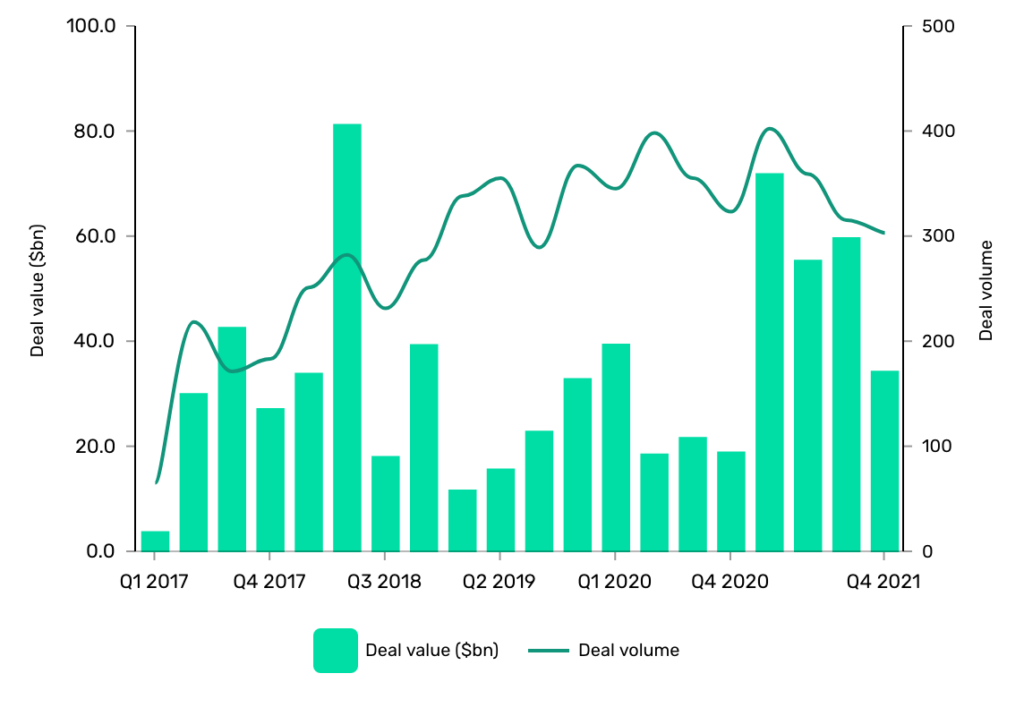
Similar spikes were seen in investment deals during the pandemic when Covid-19 created more opportunities for ransomware gangs to attack companies via their socially distanced employees. A bigger threat forced more companies to strengthen their cybersecurity, which meant more investment.
Back in 2017, GlobalData recorded 641 deals worth $103.29bn in total. Jump forward to 2021 and the number of deals had jumped to 1,383 deals worth $220.93bn in total.
The surge in cybersecurity stocks this week suggests that similar mechanisms are at work now, meaning more companies expect more hacks to come.
One can only speculate about what type of attacks will happen next following Putin’s invasion of Ukraine.
However, the sentiment in Whitehall currently seems to be that attacks against Britain will fall short of any major infrastructure attacks that would meet the threshold of the UK being forced to issue a counterstrike. Still, small-scale assaults can have massive consequences.
“It is important that business leaders recognise that it is not just large organisations or government bodies that will be attacked in cyberwarfare: any small business part of the supply chain for the public sector will be at serious risk,” Rick Jones, CEO and co-founder of cybersecurity firm DigitalXRAID, warns Verdict. “These companies will become the more penetrable backdoors for hackers.”
And with over two dozen EU members having joined the US and the UK in sanctioning Russia for its actions, it’s safe to say that its only a matter of time before an attack happens.
It is also important to caution that while the focus is currently on the war in Ukraine, none of the regular ransomware gangs have gone anywhere. As Verdict reported earlier this year, GlobalData researchers have warned that “attackers will target immature technologies, meaning 5G communications, smart cities, and the Internet of Things” in 2022.
What should businesses do?
Companies in nations that have backed sanctions against Russia should expect threats to their cybersecurity. In other words; they should strengthen their digital defences.
“Businesses need to ensure that they act fast,” says Pinson-Roxburgh. “The best way forward is a truly end-to-end cybersecurity approach. Technology and security hygiene will be [essential.]”
Experts speaking with Verdict agree that covering the basics will go a long way.
Their advice usually follows the same guidance offered by NCSC. Companies are encouraged to patch systems, improve access controls and enable multi-factor authentication, implement effective incident response plans, check that backups and restore mechanisms work, ensure that online defences work as expected, and keep up to date with the latest threat and mitigation information.
Many also highlight that the biggest threat to companies’ cybersecurity efforts continues to be human error. People’s shortcomings are behind up to 95% of all successful breaches, according to an IBM report.
Hackers are experts at social engineering techniques that trick employees into providing vital information about vulnerabilities attackers can exploit. Staff members can also fail to update software or to report suspicious activities, both of which errors could lead to successful breaches. Training staff in proper cybersecurity hygiene can go a long way.
While the war in Ukraine has only just begun, businesses failing to follow these guidelines could end up regretting it sooner than they’d expect.
GlobalData is the parent company of Verdict and its sister publications.



